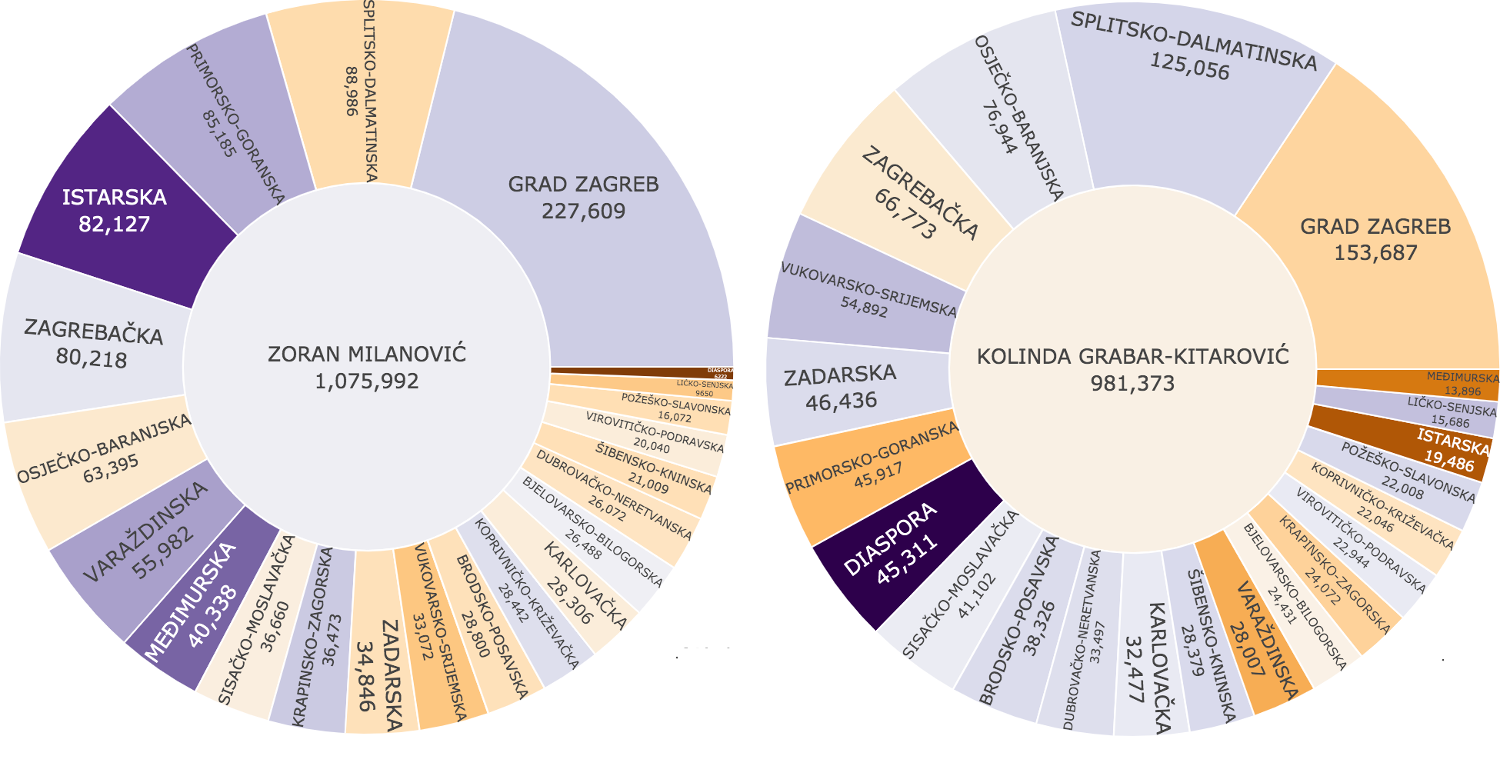
As we all know, Zoran Milanović won Croatian presidential elections and became the fifth president of Croatia. But how it actually happened? How did people vote and whose votes brought victory to Mr. Milanović?
I went to great lengths when installing OpenCV 4.1.1 on Google Coral Dev board. If you are in the same situation, you might have just found a solution! This post explains how to install OpenCV 4.1.1 and do machine vision on Google Coral Dev board.
The built-in Django User model follows the pattern consisted of username, email and password. In this tutorial you will learn to RESTfully simplify it to just email and password.
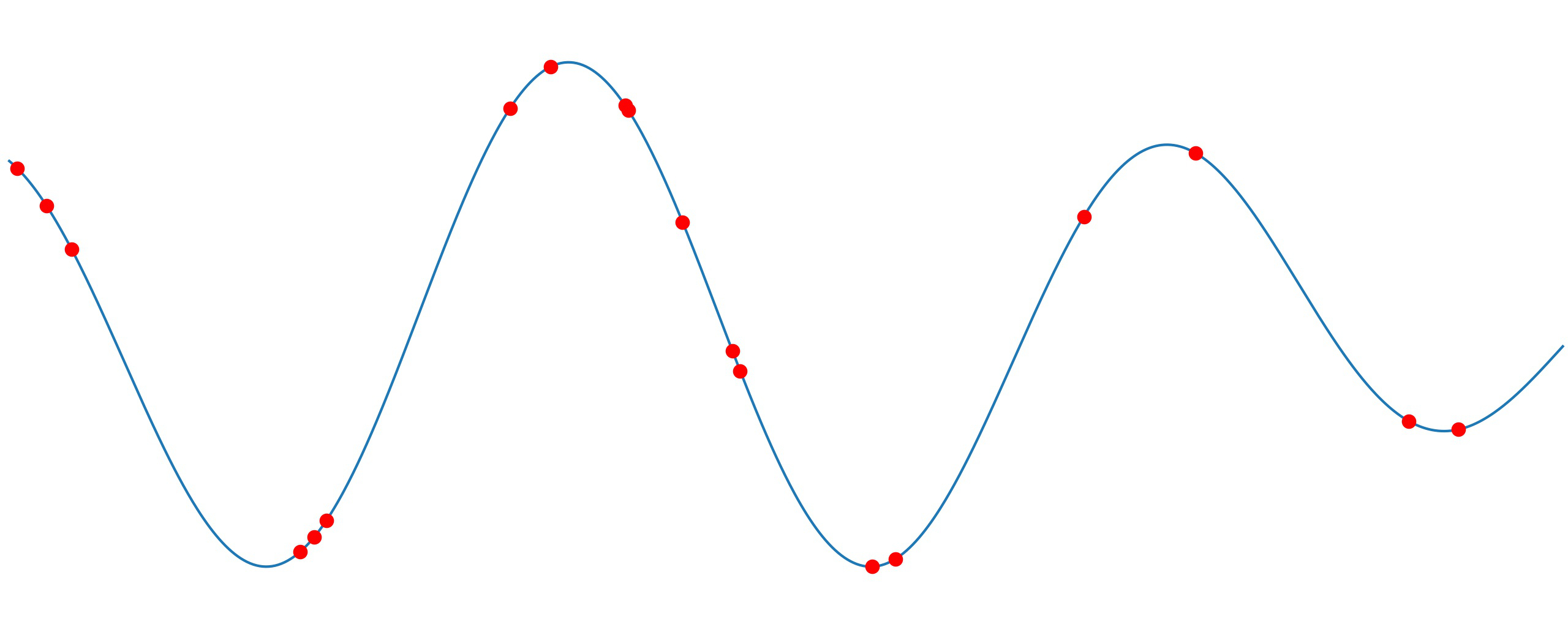
What can you do when your time-variating signal is unevenly sampled? Well, let us introduce you to The Lomb-Scargle periodogram! Because even irregulary sampled data can give you valuable results!

Our co-founder Marin Bek shared his success story with Telegram.hr. Marin is brutally sincere – talks about his ups and downs without any sugarcoating or remorse. A lot has changed since he first entered The Game. He went from working in his small apartment and borrowing sums that most people would mock – to successfully running a 20+ people operation, working with Carrefour, Nestlé, Ferrero, and Forbes, innovating in Industry40 - creating Ascalia Ltd.

Traditionally the idea of scaling in development was mostly associated with server-side applications. However, as the web applications started to become more complex with frameworks like React, PWAs, native applications, and others, the need to write scalable code has crossed to the frontend.
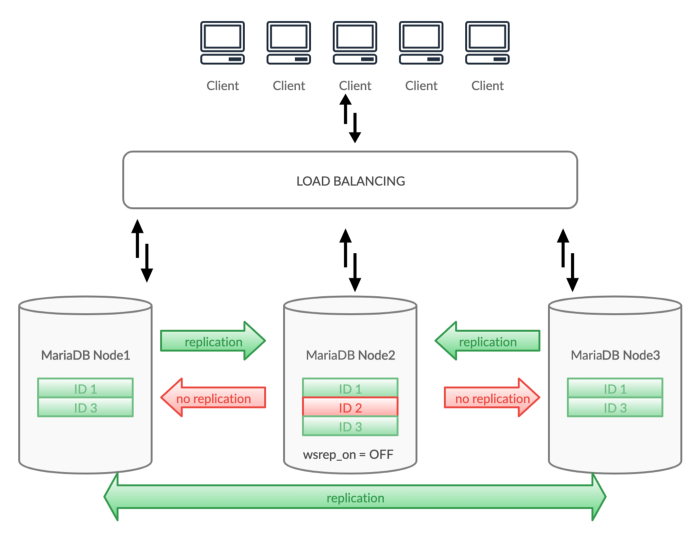
Galera Cluster is no-downtime or near-zero downtime cluster software which allows you to perform rolling upgrades or schema changes without significant effect on the application.

Now, let’s automatize sentiment analysis! In our previous article, we discussed rule-based methods and how to implement them, but here we’ll teach you how to do it simpler and quicker.

Our start-up Ascalia won the elite Start.up! Germany Roadshow pitch organized by the Association of German Chambers of Industry and Commerce and German-Croatian Chamber of Industry and Commerce

Before writing your first React component you should know how to setup your environment. Boilerplates, Webpack or Parcel, Babel, linter and dev tools are essential for bringing your React project to life.